Given the growing number of vulnerabilities and risks from cellular IoT devices, network cloudification, open-source adoption, and 5G network infrastructure evolution, the potential for new attack vectors is growing daily. Being well-prepared with robust security measures should be an enterprise imperative, enabling rapid detection & response to any potential cyber threats.
Where Should Organizations Start?
You can’t protect what you can’t see
Ensuring clear visibility of your 5G assets as a part of your attack surface risk management strategy is a critical first step. Regardless of how roles and responsibilities are allocated between businesses and partners, security visibility and consistent monitoring across the entire 5G environment is of paramount importance.
Beyond asset visibility and management, enterprises need to have security visibility across deployed user equipment (UE) or IoT devices. While it’s theoretically possible to extract asset information from the core network, in practice most enterprises lack the ability to access the core network or its internal data. Even if access is granted, important security status information will be absent. This implies that in the event of a compromised endpoint device, security team awareness would not be immediate.
Security visibility must also encompass the entirety of the 5G network system, including endpoint devices, RAN, the core network, and the enterprise IT infrastructure. An ability to have a complete view of the overall environment is essential to being able to promptly identify, contain, and address potential threats. This holistic perspective enables the ongoing assessment of the enterprise attack surface and avoids potential gaps that can increase risk.
5G supports massive scale…and that can be a visibility challenge
More and more enterprises are opting to deploy private 5G environments to support advanced new applications, but the advantages of 5G also can make security harder. A key scaling capability, mMTC (massive Machine-Type Communication), facilitates the connection of an immense number of IoT devices for unprecedented data transmission capabilities. It allows for smooth connectivity among many devices being used to drive the enterprise forward, including applications in smart manufacturing, smart logistics, and other mission-critical uses.
5G deployments are expected to drive large numbers of diverse endpoints, including many which are mobile and not always as visible as other OT devices. Enterprises should plan for the use of solution that gives them visibility across their attack surface as well as the security status of all assets in order to be ready for any potential threats.
While private 5G deployment in enterprises is currently limited, the full potential of mMTC remains untapped. As we anticipate broader 5G implementation, the challenge lies in efficiently managing the multitude of cellular IoT devices or UE deployed in the field. This task becomes even more complex when considering factors such as security protocols and ever-evolving threats.
Getting aligned with executive expectations of 5G security
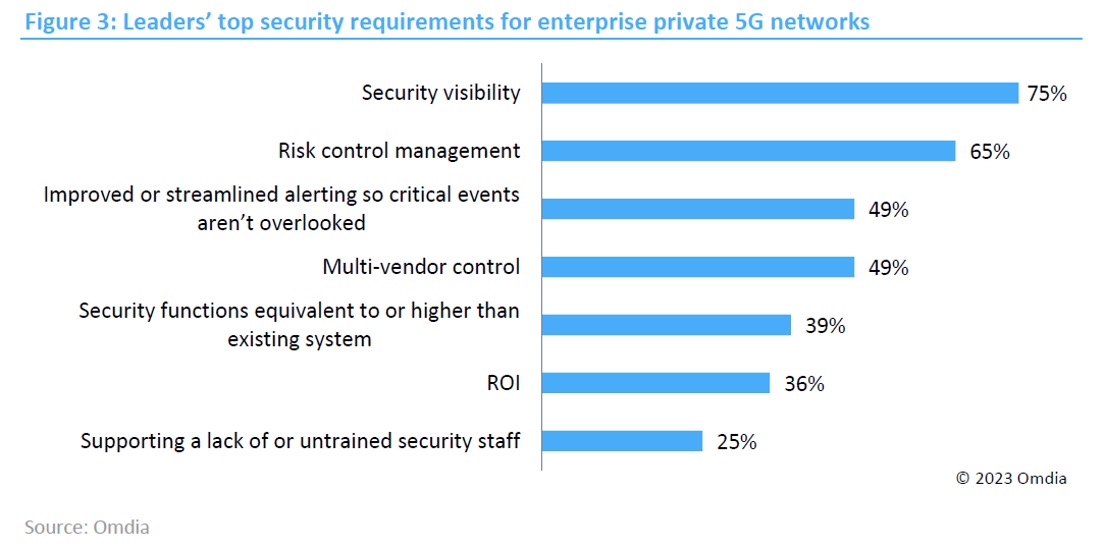
According to our latest research report produced in collaboration with Omdia, CTOne, and Trend Micro, when considering security requirements for enterprise private 5G networks, business leaders’ (C-level or management team) top three expectations are focused on security visibility (75%), risk and control management (65%), and improved and streamlined alerting system (49%). This highlights the importance of organizations investing in security as an inherent part of the deployment strategy.
Risks, risks, everywhere!
In a world where the enterprise attack surface is continuously shifting and expanding, it’s critical that organizations understand where the risks are…and what to do about them. Areas for organizations to focus on include:
Unpatched n-Day vulnerabilities
Many IoT devices do not have the ability to easily install (or at all) agent-based security solutions. This means that even if a device is able to be patched,
there will typically be a time gap that introduces risk, especially where devices are a part of a critical infrastructure where downtime must be scheduled.
SIM swapping
Stolen SIMs can lead to a compromised network and potential access control risks introduced by using a
SIM in the wrong device.
Risks from software defined radio (SDR) devices
Attackers may target devices using SDR and craft malicious or anomalous signaling packets as a part of an attack. Normally users can’t send crafted signaling messages from normal UE because this part is handled by an internal modem, but with SDR devices the user can change signaling message packets which can expose potential risks to enterprises.
Recommendations for 5G security
We recommend the implementation of a robust Zero-Trust strategy, focusing on strict identification and management of endpoint devices. This approach ensures that regardless of the device’s origin or location, it is subject to stringent identification and verification measures before being granted access. Alongside this, we emphasize the integration of an action and response capability. By swiftly detecting and responding to any anomalous activities or potential breaches, organizations can effectively stop threats before they escalate. Finally, we recommend that organizations focus on moving beyond asset visibility to include enhancedsecurity visibility that delivers an intuitive management experience for the team. Expanded visibility empowers IT and InfoSEC teams to proactively monitor and address new risks from 5G implementations.
To learn more about how our solutions can help with expanding attack surface risk from 5G, please visit: Solutions – CTOne
More To Explore

Salt Typhoon Has Telecom Industry’s Number: Understanding New Attacks & Threats to Critical Infrastructure
2 mins. read














