Standalone vs Hybrid Private 5G Environment
Traditionally, manufacturing environments are isolated physically and wireline connected; thus, it is secured from outside access theoretically.
Take a manufacturing plant for example, a private 5G network seamlessly connects numerous IoT devices to the cloud-based 5G core and backend servers. These devices operate within a secure private IP subnet, rendering them inaccessible from external networks. Notably, these IoT devices have restricted internet access, enhancing their security and control measures.
However, in practice, the feasibility varies based on distinct use cases, performance requirements, and cost-effectiveness. Not all enterprises are suitable for establishing a standalone 5G NPN (non-public network) in a complete isolation architecture. More and more, the hybrid NPN architecture gains popularity, and a more advanced examination of 5G security concerns becomes warranted.
Common configurations while implementing a private 5G network (Source: 5G-ACIA):
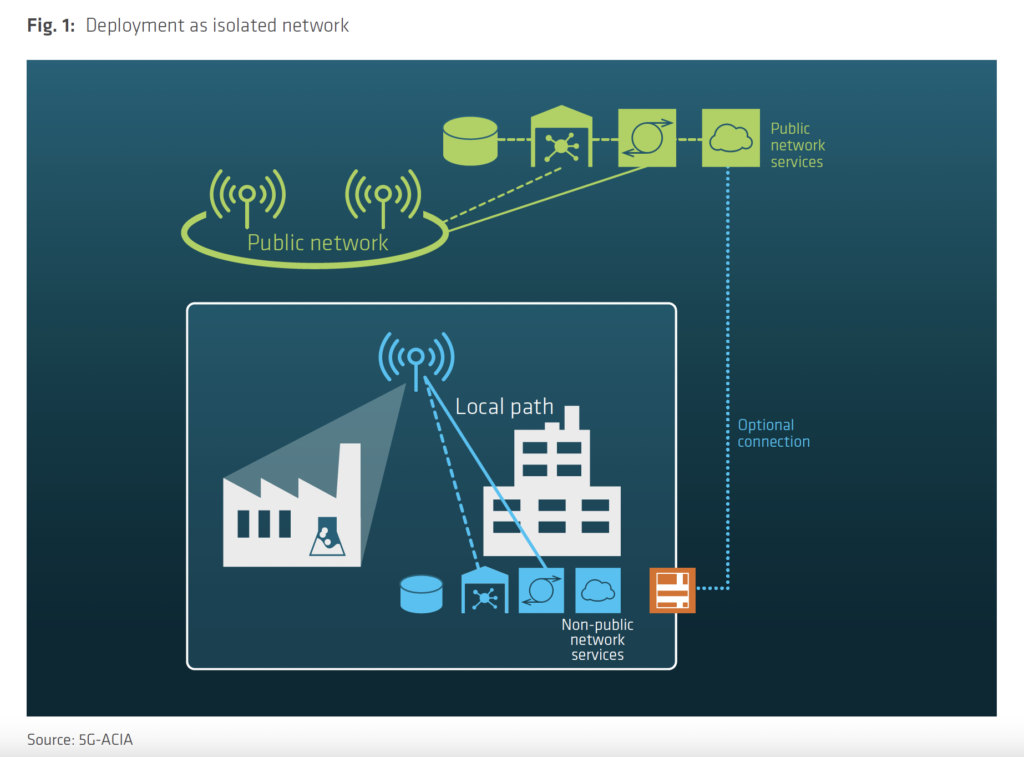
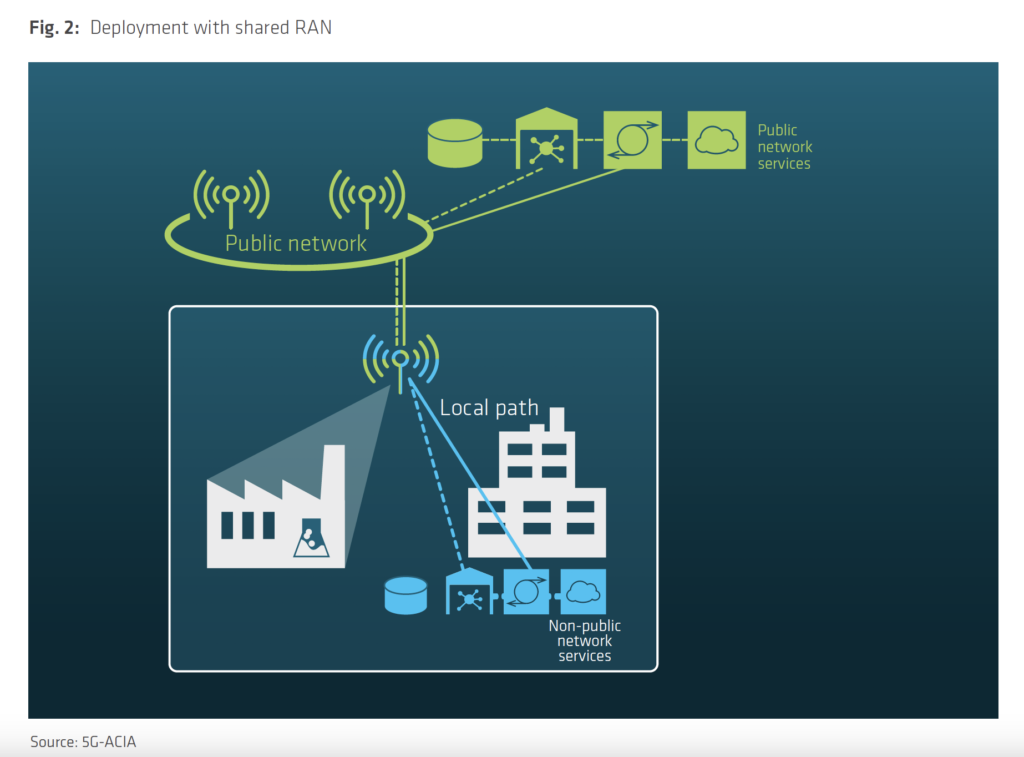
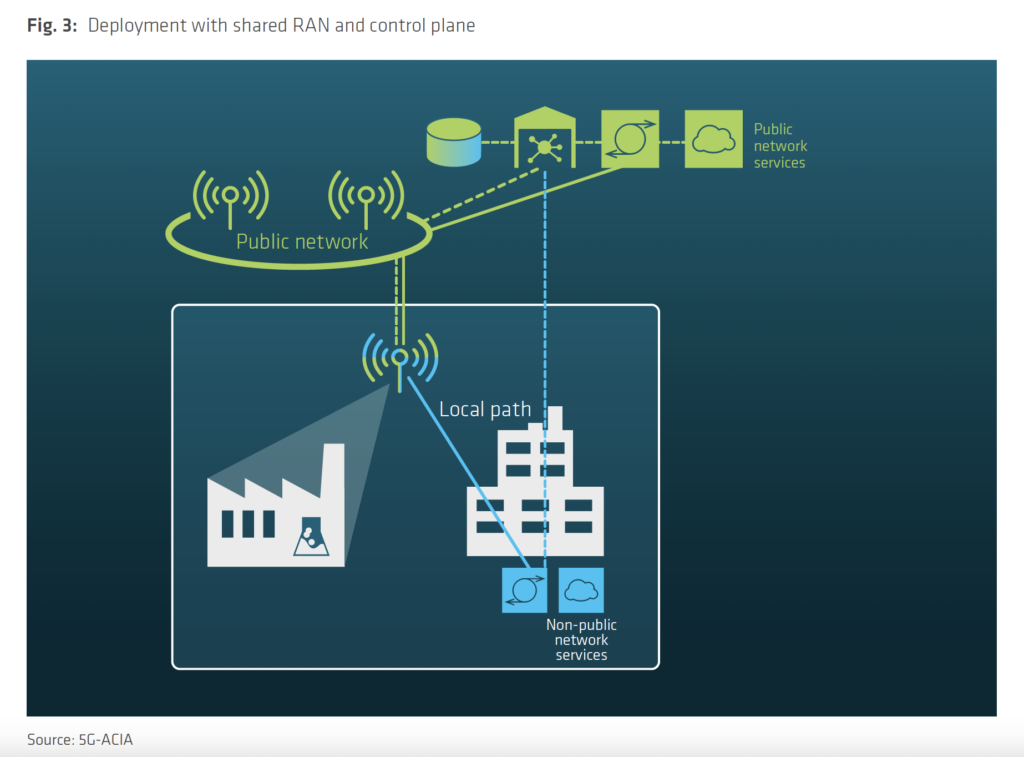
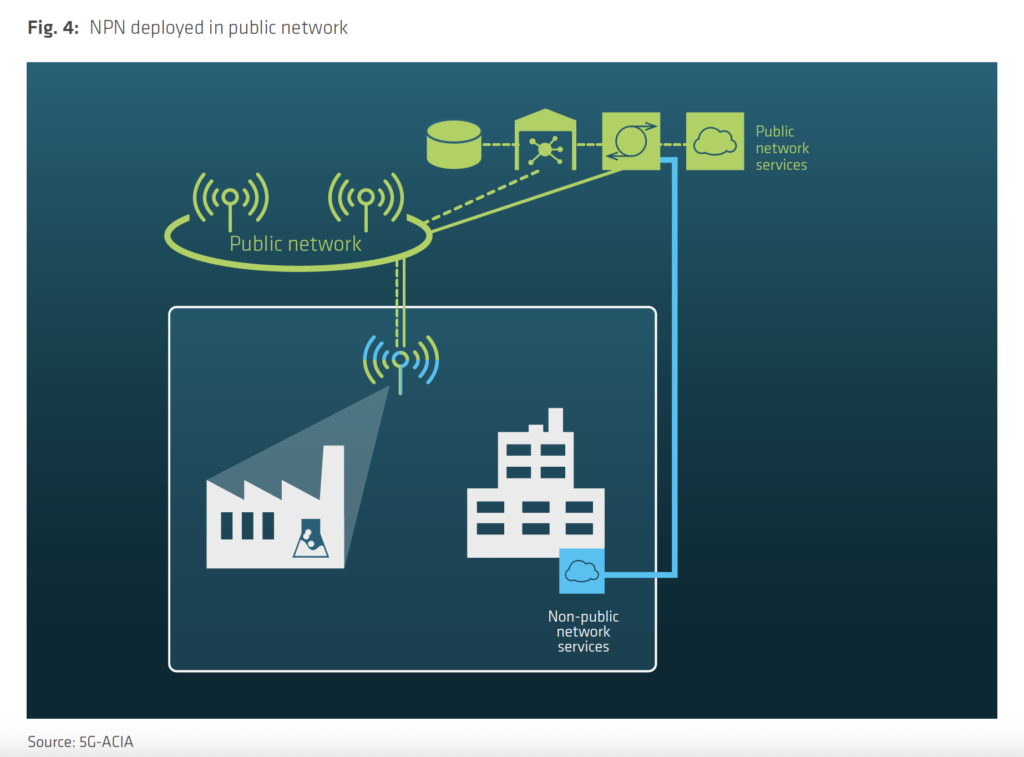
General Security Challenges From Close to Open
In the realm of hybrid environments, the 5G system is poised to interface with an open environment. Despite 5G connectivity being widely acknowledged as the safest wireless communication technology nowadays, the transition from a closed to open architecture, the implementation of network function virtualization, the utilization of open-source resources, and the numerous unprotected IoT devices expose 5G to different types of vulnerabilities and potential attacks.
The latest report from GSMA (GSMA | Private 5G Industrial Networks 2023 | Internet of Things) provides a comprehensive perspective on the significance of private networks within the industrial and manufacturing sectors, outlining the requisites for such networks. In relation to security, one of the highlights of the report is the necessity for 5G private network service providers to address security measures for conventional OT devices and operations. Consequently, in the process of designing private networks, comprehensive cybersecurity planning should be given to the attributes offered by the 5G private network service provider.
The released report from NIST SP 1800-33B also addresses the challenge that organizations face when planning to deploy, operate, and use 5G networks. While standards for certain 5G cybersecurity features have been published by standards bodies, these organizations struggle to determine the security capabilities that 5G can provide and how to effectively deploy these features to safeguard data and communications.
Our Use Case
CTOne has collaboratively partnered with numerous 5G private network service providers to validate and adopt our solution into their services, delivering a secure private 5G network for enterprises.
View one of our successful cases in smart manufacturing: Accelerating the Digital Transformation in a Smart Factory – CTOne
Conclusion
In conclusion, the conventional notion of secure manufacturing environments, isolated physically and connected by wired lines, is evolving due to the rise of private 5G networks. Theoretically, such networks offer enhanced security through private IP subnets and restricted internet access for IoT devices, preventing external access. However, practical implementation varies based on use cases, performance needs, and cost considerations. The hybrid approach gains traction, demanding a deeper look into dedicated 5G security before and after the operation.
More To Explore

Salt Typhoon Has Telecom Industry’s Number: Understanding New Attacks & Threats to Critical Infrastructure
2 mins. read














