Summary
With geopolitical challenges on the rise around the world, critical infrastructure, including telecommunications, has become a prime target for hackers. With customers and specialized cybersecurity solutions for the telecom industry, CTOne has significant visibility into these types of attacks, giving us unique and valuable intelligence that powers our enterprise solutions.
Overview
Since 2023, the Chinese APT group Earth Estries (aka. Salt Typhoon) has primarily employed IT-focused attack techniques to compromise more than 20 known organizations across a range of sectors including telecommunications, technology, consulting, chemicals, transportation, as well as government agencies and NGOs across multiple countries
A recent blog from Trend Micro shows that victims came from numerous countries, including: Pakistan, the Philippines, South Africa, Taiwan, Thailand, US, Vietnam, Afghanistan, Brazil, Eswatini, India, Indonesia, Malaysia, and more.
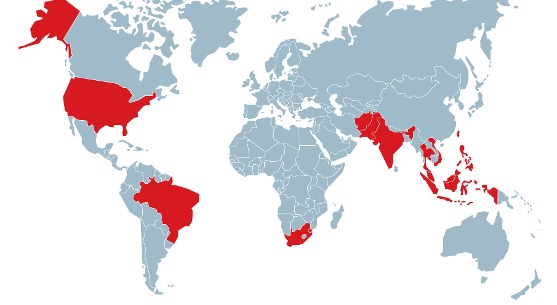
Victimology map of Earth Estries, Source: Trend Micro
A key finding from Trend Micro’s recent investigation also uncovered a new backdoor, GHOSTSPIDER, identified during attacks targeting Southeast Asian telecommunications companies.
In this blog, we will explore some of the common attack paths targeting telecom infrastructure via C2 servers as well as discussing our approach to defending against these attacks.
What are C2 servers?
C2 (Command-and-Control) servers are used by attackers to remotely manage and control compromised devices or systems within a network. The C2 server acts as the central hub for the attacker to send commands, execute malicious actions, and exfiltrate data from infected machines.
Additionally, C2 traffic is often encrypted with TLS, making it challenging for standard security solutions to inspect the contents and detect attack patterns. As a result, once the C2 connection is established, identifying attacks initiated by the C2 server becomes extremely difficult for defenders.
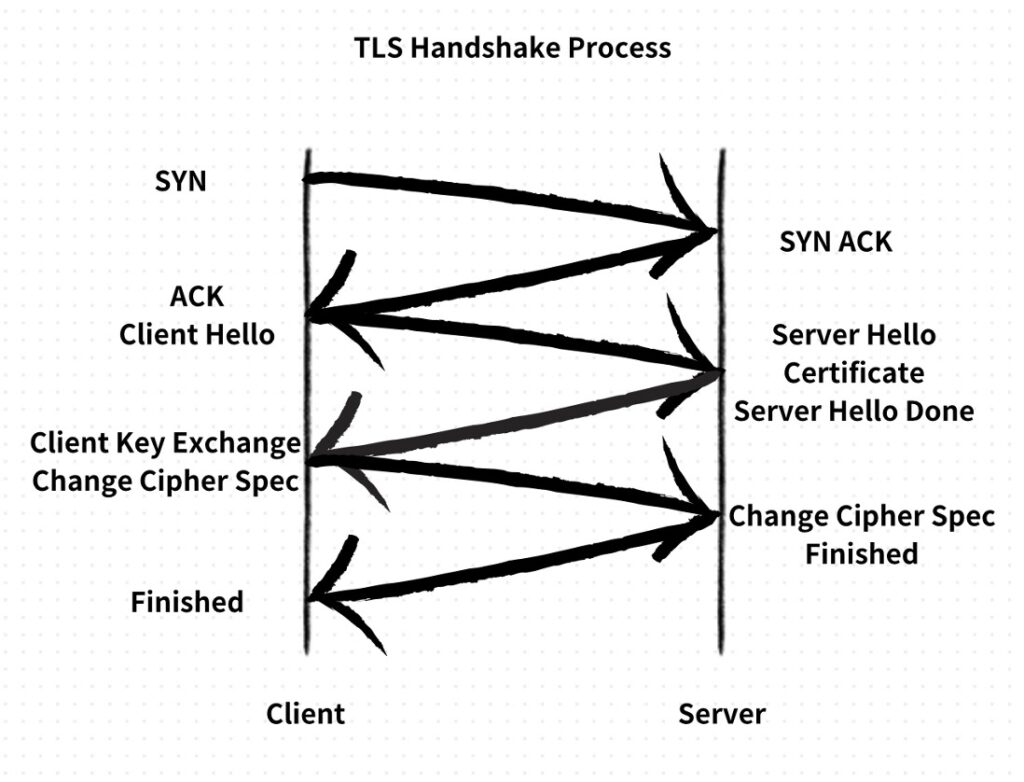
TLS handshake process. Source: CTOne
Attack Paths
We found that while attackers primarily use IT-based techniques to target CT (Communication Technology) infrastructure, such attacks can occur in both IT and CT networks. Additionally, there is potential for more CT-based attack techniques to be exploited in the future.
The diagram below first illustrates a common approach for attackers to exploit existing vulnerabilities in security solutions like IPS, NGIPS, firewalls, and IDS within IT networks to penetrate CT networks and establish communication with the attacker’s C2 server.
Another possible attack path involves exploiting vulnerabilities in IoT (and Cellular IoT) devices, or devices connected to them, within CT networks to establish a connection between the attacker’s C2 server and CT infrastructure. Learn more about the latest in CIoT threats here.
Without clear visibility into both IT and CT-specific threats, defending against C2 connection establishment and subsequent attacks is impossible.
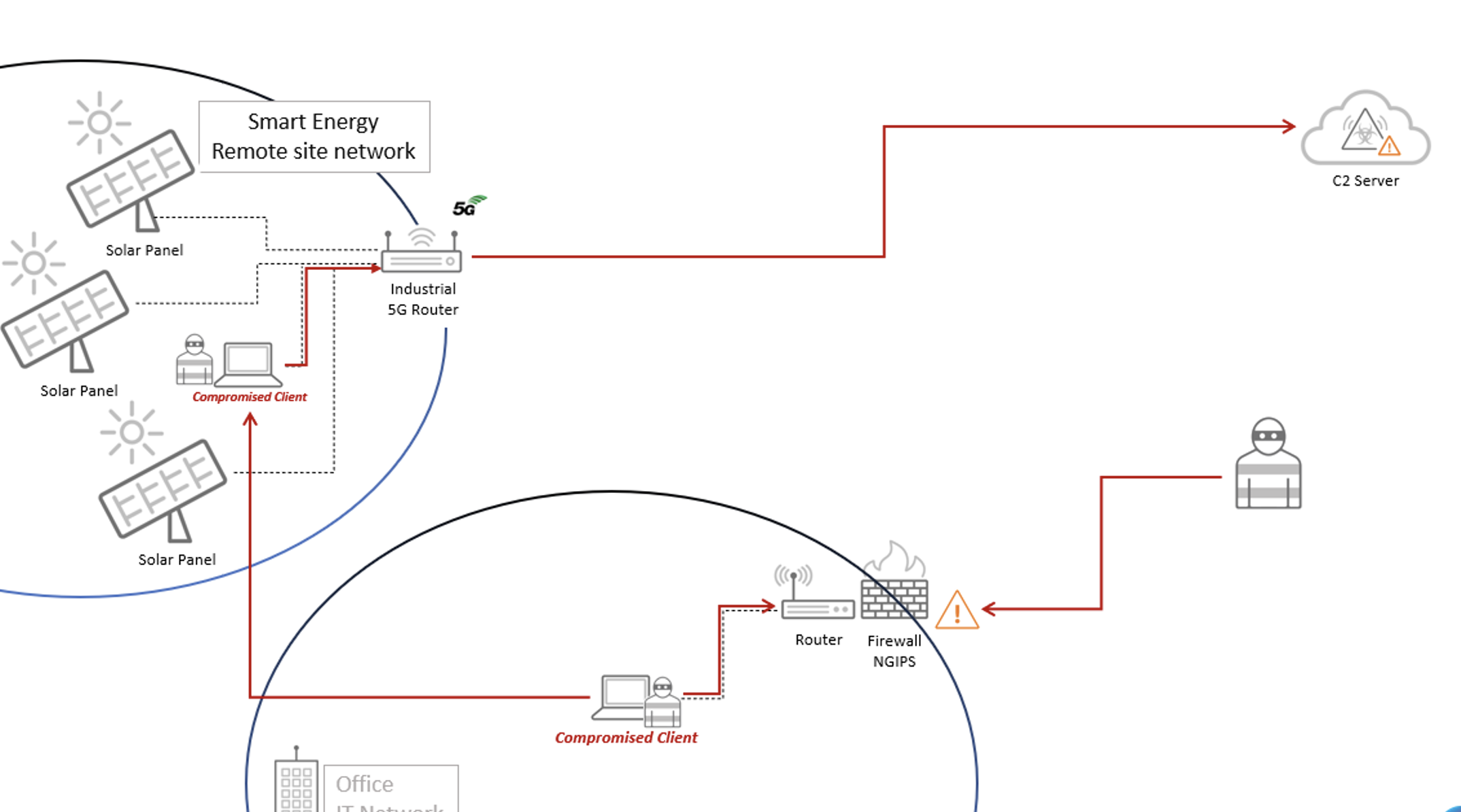
One of multiple possible attack paths in telecom networks. Source: CTOne
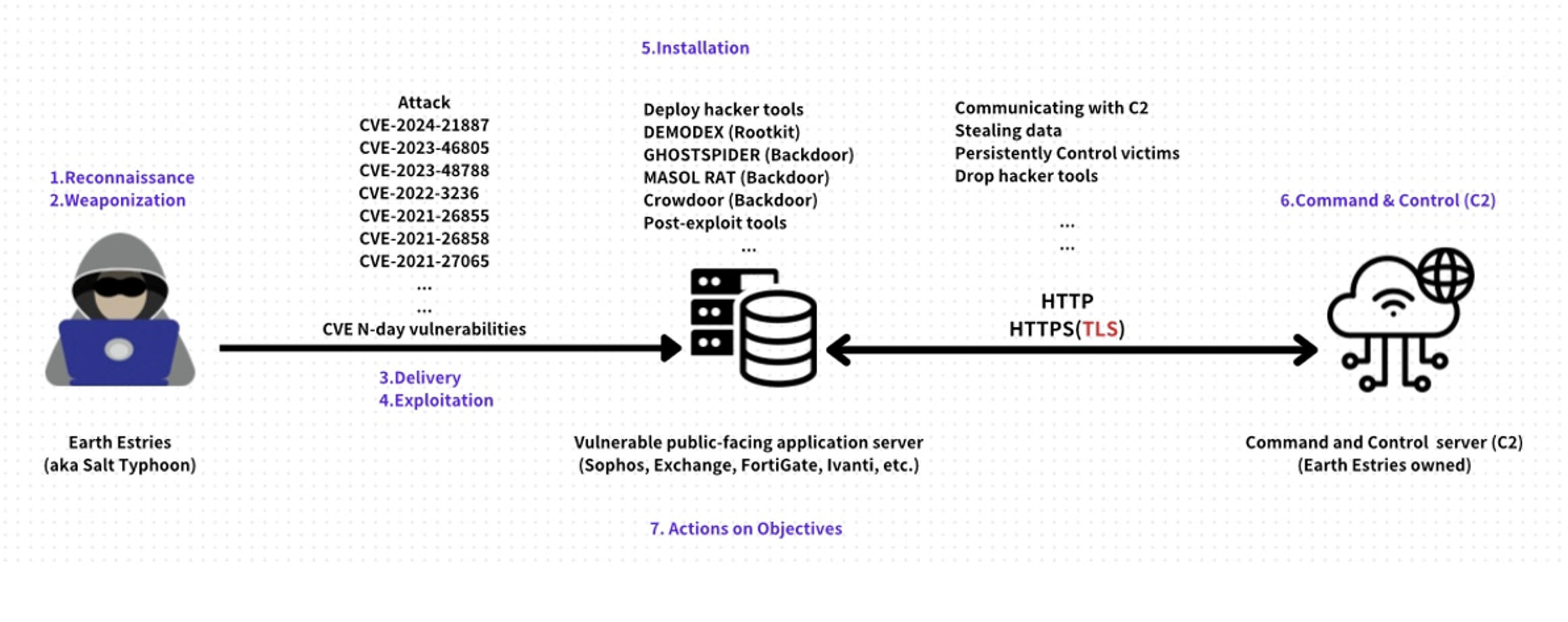
Cyber kill chain by Salt Typhoon. Source: CTOne
Mitigation plan
CTOne specializes in detecting and stopping attacks within CT networks, including IT threat identification. In an increasingly connected world, the scope of threats continues to evolve, and CTOne. offers enterprise solutions to prevent attacks like those from Salt Typhoon. Complementing this, our expert TR2 team is dedicated to understanding and mitigating these targeted threats to the telecom industry, regularly updating the threat database used by CTOne solutions to help manage current and emerging CT risks.

CTOne mitigation plan. Source: CTOne
Contact us today to learn more:
[email protected]















