The conventional view that private 5G networks are unbreakable because they are isolated and more secure than older technologies (3G/4G) is a common one. Spoiler alert: there are still risks! Despite rigorous testing and certification required before installation, anomalies and potential security breaches can – and do – occur due to diverse usage patterns and many different types of applications.
While new types of communication technologies (CT) are not yet common targets, exploits and attacks used against traditional IT deployments can still impact private network deployments.
This case study highlights an recent event that occurred in a private 5G environment, demonstrating that these networks may not be as “private” as assumed, and in the end, how CTOne helped the customer to proactively understand and mitigate the issue and risks from it.
Background
During a recent digital transformation project, the organization looked at the options for networking and chose private 5G over Wi-Fi. Driven by the deployment of on-site AI applications and their need for high transmission speeds, wide bandwidth, and extensive IoT device connectivity, the criteria driving their choice was the requirement to ensure a more secure connection that included enhanced stability and network quality.
While access to the private 5G network is selectively provided to specific users and applications, it is easily accessible based on the submission of a simple web request. Consequently, monitoring for abnormal events or misuse of the 5G service is essential, combined with the ability to proactively respond to the detection of any unusual behavior.
With the potential to expose sensitive user information, the organization was especially risk averse, working with CTOne to prioritize security alongside performance, emphasizing visibility and the ability to fully understand their security posture and manage risks effectively within their new private 5G network.
Customer Project
The organization is leveraging private 5G for public area use. Upon approval, individuals are able to access private 5G network services for applications using AI, AR, VR, and automated guided vehicles (AGV).
Private 5G Environment
- No Operator, only system integrator and service providers provide the complete private 5G environment
- RAN/5GC provider dependent
- 5G Standalone (SA) architecture
- Dedicated spectrum for private 5G network
- Number of UE: over 100 Endpoints on the fields
Event Details
The customer’s private 5G deployment was operational and effectively supporting key applications. However, leveraging the CTOne solution, abnormal events were detected at N3 from various endpoints, involving TCP SYN Flood and ICMP Flood, and the data traffic was blocked at N3.
The logs indicated a significant number of TCP SYN packets were potentially being sent from an approved endpoint device. The ICMP flood detected had an ICMP Type of Destination Unreachable (ICMP type 3). These ICMP unreachable messages can be generated due to TCP, UDP, or ICMP messages. UDP flood/scan is the most common cause of these ICMP unreachable messages.
Expert info
What is a SYN flood attack?
A SYN flood, also known as a half-open attack, is a type of denial-of-service (DDoS) attack designed to render an IT server unavailable to legitimate traffic by exhausting its resources. This is achieved by continuously sending initial connection request (SYN) packets, overwhelming all available ports on the targeted server. As a result, the targeted device responds sluggishly or fails to respond at all to legitimate traffic.
What is a Ping flood attack?
A ping flood is a denial-of-service attack where the attacker floods a targeted device with ICMP echo-request packets, aiming to overwhelm it and render it inaccessible to normal traffic. When this attack originates from multiple devices simultaneously, it escalates into a distributed denial-of-service (DDoS) attack.
For the observed behavior, the relevant attack vectors are both connected devices and remote.
User Equipment (UE) such as mobile phones and cellular IoT devices. Also includes SDR UEs.
Adversary can execute these attacks from external networks by sending network packets.
The CTOne Solution
CTOne delivers a joint defense solution for securing private 5G deployments, including protection across the endpoint and network layers:
Endpoint layer:
- CTOne SIM card solution with endpoint protection
Network layer:
- TMMNS Inspector deployment: N3
- Mode: Inline
- Host OS: RHEL 8
- Hypervisor: KVM
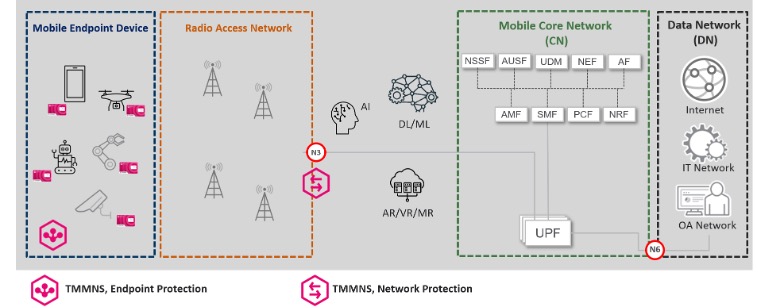
*Solution Deployment
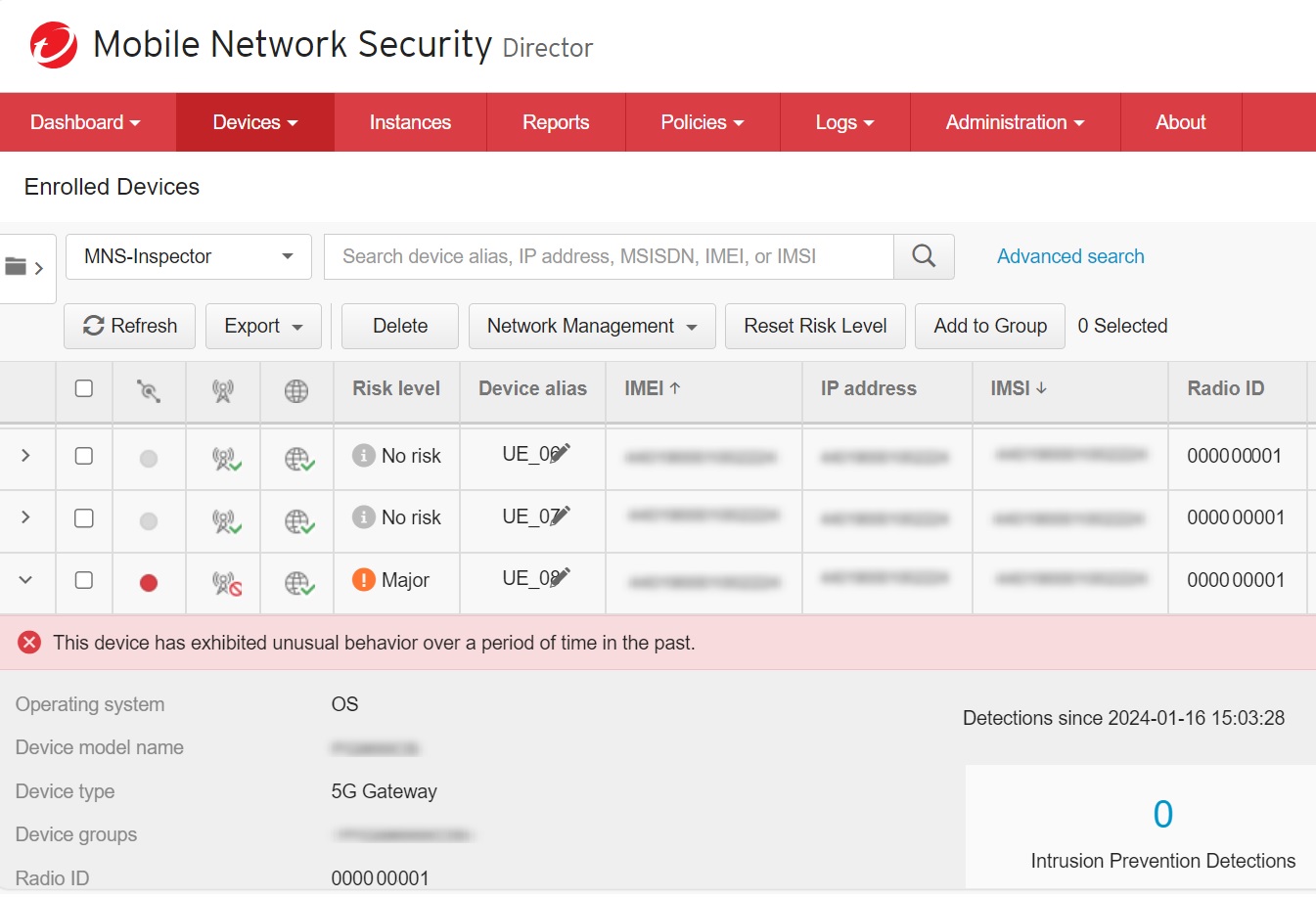
*Management console for real-time endpoints’ security visibility
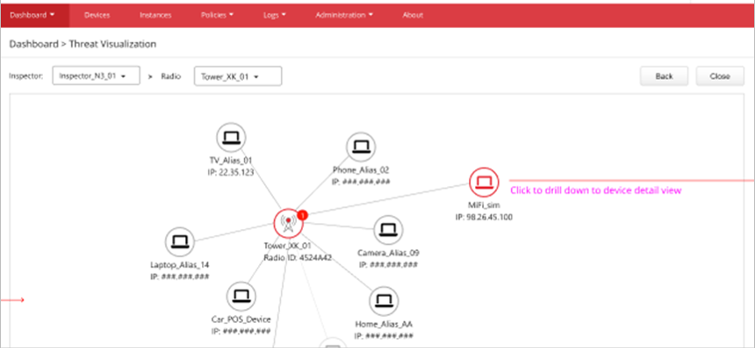
*Threat Visualization
Key Findings
- Private 5G, like IT networks, are susceptible to attacks. In this use case of a private 5G network that is open to the public or accessible to specific users with minimal vetting increases the possibility of different types of attacks.
- Abnormal behavior could potentially negatively impact the performance of 5G application services from various forms of DDoS attacks.
- While the vulnerability in this case does not directly involve the 5G core itself, this example demonstrates that private 5G networks can be disrupted from the endpoint, highlighting its vulnerability despite being perceived as a closed and secure environment. To learn more about the 5G vulnerabilities discovered by CTOne’s threat experts, please visit:
❖ The imperfect 5G core network infrastructure platform may become a potential cybersecurity vulnerability for enterprises – CTOne
❖ Attacks on 5G Infrastructure From Users’ Devices | Trend Micro (US)
❖ Attacks on 5G Infrastructure From User Devices: ASN.1 Vulnerabilities in 5G Cores | Trend Micro (US) - Even though it may be considered a typical IT incident, without a security solution deployed with N3 inspection capabilities, the traffic remains invisible. Meanwhile, if an enterprise only deploys an IT firewall at N6, it will miss the attack, as they originate from the endpoint rather than the data network side.
- Our joint defense approach performed flawlessly, not only blocking the traffic at N3 but also automatically severing connections to corrupted endpoints and stopping them from executing further attacks.
- The impacted endpoints were quickly identified and displayed on the CTOne management console, highlighting the power of real-time monitoring of private 5G security events.
More To Explore

Salt Typhoon Has Telecom Industry’s Number: Understanding New Attacks & Threats to Critical Infrastructure
2 mins. read














